Blackmail viruses: 10 most serious threats posed by ransomware
7 min readTable of Contents
Jaff – Massive spam campaign
Jaff is a strain of ransomware that is very similar to Locky. At first glance, it is quite simple and yet, or perhaps just because, very successful. It also spreads as spam and uses botnet Necurs to send malicious emails. It addresses potential victims at an impressive rate of approximately 5 million e-mails per hour.
Like many other variants of ransomware, Jaff comes as a PDF attachment. When the user opens the file, a single-line document appears and a pop-up window asks if he wants to open the embedded document. If so, the MS Word document opens with instructions on how to turn off macro protection.
If this user also trusts and enables macros, the Jaff binary file will be downloaded. This is followed by the traditional encryption of documents and the requirement to pay the ransom. For more details, the user is directed to a page on the dark web.
Compared to Locky and similar ransomware, Jaff can be described as relatively expensive. If users want to recover their encrypted files, they have to pay a ransom of almost 3000 USD. Most of the ransomware will be satisfied with a ransom of hundreds of USD.
Cerber – ransomware as a service
Cerber is an example of where ransomware technology is evolving. It is offered as a ransomware-as-a-service (RaaS). In practice, this means that anyone can buy an attack in exchange for forty percent of the money received.
Cerber targeted the Office 365 cloud users with a sophisticated phishing campaign that affected millions of users around the world. It was particularly successful in post-Soviet countries such as Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine or Uzbekistan.
The attack is done so that the victim receives an e-mail with an infected Microsoft Office document attached. Once running, ransomware can run silently in the background during the encryption phase without raising any suspicion. When encryption is complete, the user finds the ransom information in the encrypted folders and often in the background wallpaper.
At its peak in early 2017, Cerber accounted for 26% of all ransomware infections. It uses strong RSA encryption and there are currently no decoders available to recover the encrypted files.
Ryuk – bitcoin memories
Ryuk is part of a relatively new family of ransomware that was first recorded in August 2018.
Unlike ransomware that exploits security holes or spam, Ryuk is used to target specific organizations. It focuses mainly on large goals, which can be expected to pay a lot of money to restore their files.
Ryuk uses robust algorithms such as RSA4096 and AES-256 to encrypt files. Subsequently, it requires payment of ransom ranging from 15 to 50 bitcoins.
Its creators have already earned 4 million USD, which they received in 52 payments.
Experts have initially assumed that Ryuk has its roots in North Korea based on source code studies. They assumed that most of the code was identical to Hermes’ ransomware, however, further investigation showed that the authors probably came from Russia and built the malicious application on the stolen code.
Dharma – Enter your password!
Dharma is a cryptovirus that uses contact email and random letter combinations to identify encrypted files. It first hit the world in 2016, but its authors regularly release new versions. The latest versions of 2019 change the file extensions to .gif .AUF, .USA, .xwx, .best, and .heets.
This malicious code was most successful in November 2018, when it infected a hospital in Texas and encrypted many stored records. Fortunately, the hospital was able to recover from the attack without paying a ransom.
The latest variants are still distributed via junk mail containing an attachment. The user is persuaded by the contents of the message to open the attached file – if user does so, user is prompted to enter the password contained in the text.
Then you will download the self-extracting archive named Defender.exe and uninstall the ESET antivirus program (if installed on your computer). ESET graphical user interface distributes the user’s attention during encryption. After encrypting the files, a traditional ransom request follows.
Bitpaymer – do not spare the victims
Bitpaymer is a novelty on the ransomware scene – it was discovered in July 2019, according to Symantec. While most ransomware authors focus on the intervention of a large number of victims, who demand a relatively low ransom, Bitpaymer certainly does not spare their victims. It focuses on large organizations that require amounts in the range of 100k to 250k USD.
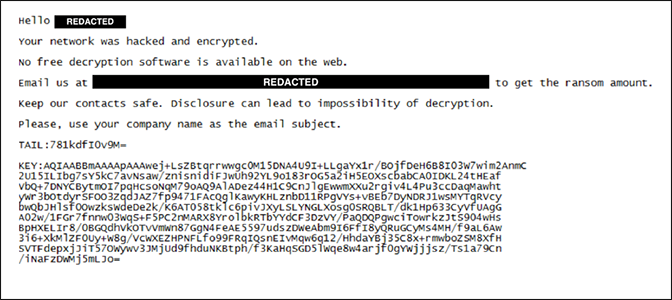
In addition to encrypting the files, ransomware runs the risk of sending confidential data to the media if the ransom payment requirements are not met. Sophisticated and trained, ESET has traced its origins – behind Bitpaymer is the creator of Dridex – the infamous Trojan horse, which has caused confusion in the banking industry.
Trojan terminates database server processes on the infected computer and encrypts all files, changing their extension to .lock. In addition, it deletes all shadow copies to prevent the computer from being restored to a previous state.






