How the controversial program that steals women’s swimsuits works? Do they have anything to worry about?
3 min read
Would you like to see any celebrity without underwear? What about the attractive neighbor you have on Facebook? Or half-forgotten high school classmates and high school assistants?
Of course, DeepNude caused a frenzy of interest, especially among men. The Estonian Web site, under enormous pressure, preferred to close down. It was all too simple. Just run the application, upload any image and clever algorithms, and the sweaty processor – or better yet, the CUDA graphics chip and did wonders.
While DeepNude has already disappeared from the official site, web soon filled up with its other implementations.For exaple here and here , where you can upload a few pictures online, but results are very funy. For the better results use the bikiny picture. One software for Windows you can download here.
In one out of ten cases the transformation of a harmless picture into a controversial one is succeed and there was indeed a risk of abuse. Especially if any amateur graphic artist in any raster editor would play with the finalization of such fictional photography. Often it is enough to merge colors and fix some slight deformation with a liquid brush.
Considering what people are willing to believe on social networks, the naked figure of someone known might well share the same fierceness as any hoax of recent years.

At the same time, the quality of the transformation will continue to improve in the context of further developments, so in a few years we will see a situation where we can question any audiovisual recording of reality.
Pix2pix
But let’s leave the social dimension aside and go back to technology itself. DeepNude is not a breakthrough. Just their app. In fact, it is just another variant of the adversial network GAN (generative adversarial network), which is one of the neural network families, which, in the case of graphical data, can uniquely transform input pixels into output pixels.
Just a few years ago, the team at the University of California, Berkeley, under the leadership of Phillip Isola, popularized the work with graphic data, who created a program using GAN to create a photorealistic version according to the sketch of the handbag, or a different photorealistic picture of the street according to different color areas where each object matched a shade. A street that doesn’t really exist anywhere in the world.
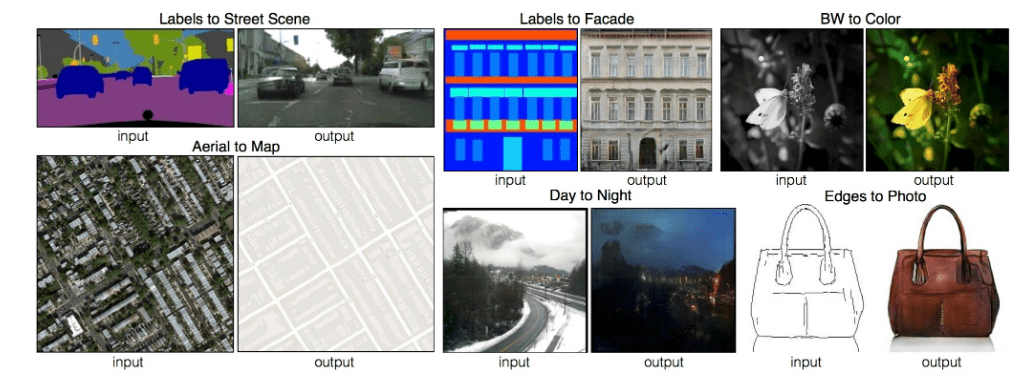
Isool’s work under the generic name pix2pix has seen many other implementations, and today a whole host of transformation algorithms are built on this technique, many of which offer live demonstrations on GitHub. For example, an Image-to-Image Demo by Christopher Hesse, where you can use the mouse to draw for example the cat on the screen and the neural network really creates it as shown.
How? It learned what contours correspond to what parts of her body, so when you draw a round head and two wheels in the middle, it estimates that it is an eye and tries to generate it.
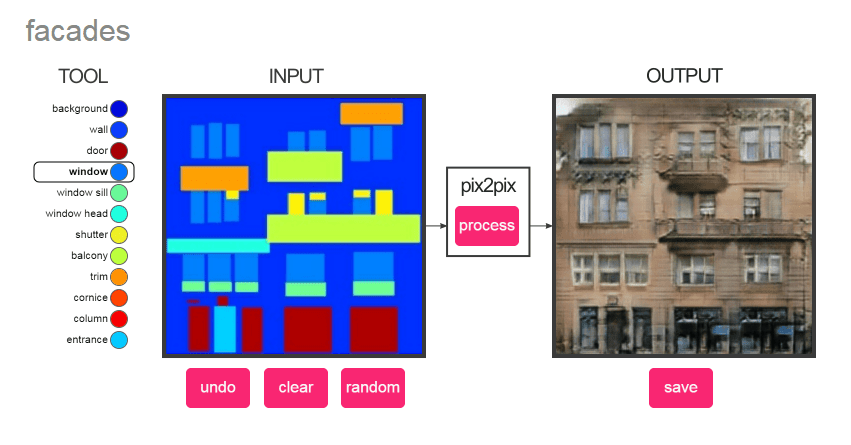
And finally we are getting back to DeepNude, which is also based on pix2pix technology. This time, the program does not transform the drawing into a non-existent photorealistic cat, but does the same thing with a two-piece swimsuit because learned how a woman’s body and its parts look like. According to the specific human figure simply calculates the female bust and possibly the wedge.
PepeNude and the army of others
For ethical reasons, GitHub doesn’t like it too much, so it tries to restrict access to these projects. For example, only logged-in users can access them. Thanks to this, today you can find on GitHub a copy PepeNude, whose code the author has posted for other similar services, so it just not disappears from the Internet.

Applicants will download everything in several ZIP packages whose aggregate size is several gigabytes. The program then works either as a text application for easy scripting and automation or in a graphical interface in which you just open any photo, in the case of a CUDA-enabled graphics card check the box and press Process!
Then just wait from a few seconds to minutes – depending on the hardware of your computer – you can embarrassingly blush looking at undressed Facebook friends, which unfortunately just turned into just a matter of sexual interest. Congratulations…