The ‘Phobos’ Ransomware Is Getting a Stealth-Boosting Upgrade
3 min read- Phobos has received some updates that are geared towards file-less payload delivery and execution.
- The actors behind the otherwise unsophisticated ransomware strain are more focused on cyber-espionage.
- In one case, they managed to roam in a company’s network for eight months while staying undetected.
The latest variants of the “Phobos” ransomware may be especially hard to detect, as according to a technical report by researchers at Morphisec, the malware authors have incorporated some new evasive tricks on it. The sampled variant was taken from an attack that happened in March on one of Morphisec’s clients, so it was an opportunity for them to analyze it and figure out what has changed compared to previous versions.
The actors encrypted a backup server which was what raised the alarms, but as the investigators subsequently revealed, the Phobos hackers were actually on the network for a total of eight months, planting several botnets and even miners. The compromise came through a brute-forcing attack on the admin’s password and the creation of backdoor accounts. So, how did the actors manage to stay undetected for so long?
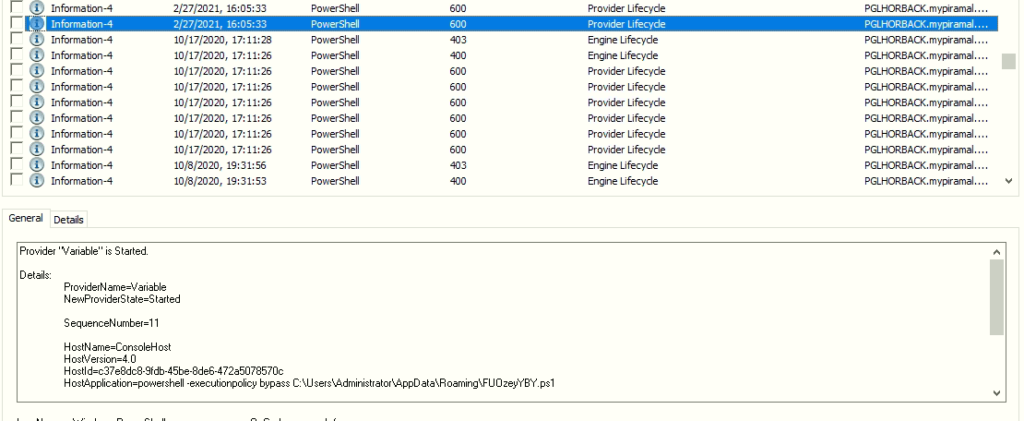
First of all, the initial-fetcher PowerShell script used was base64 encoded, and even when decoded, it remains obfuscated. The payload downloads happened through paste.ee, which is an alternative to Pastebin and follows a string replacement process which leads to hollowing a legitimate MSBuild.exe process.
The loader is obfuscated using an Agile.NET tool, replacing the previously used Vapor. As Morphisec explains, this gives better chances to evade detection from AV tools, as confirmed through VirusTotal checks.
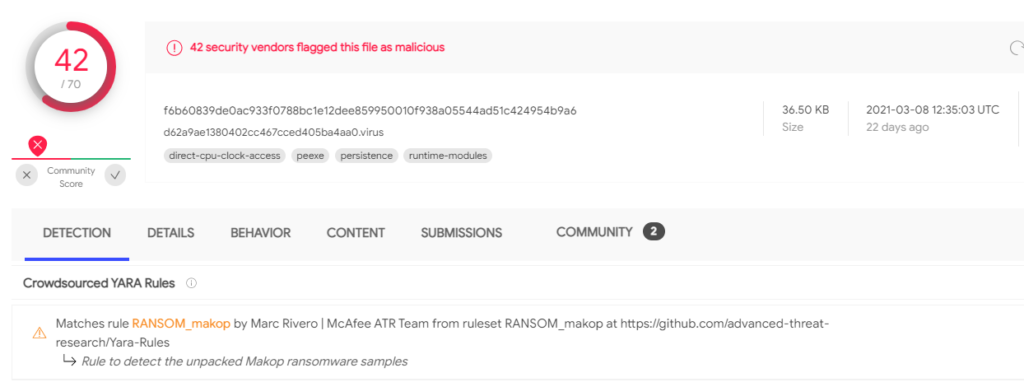
The ransomware payload itself is being detected by 42 out of 70 AV engines. Still, if it’s executed directly from memory, it could do the dirty job without giving security tools any chance. For this reason, the actors are now engaging in file-less delivery, which makes the threat so much more potent.
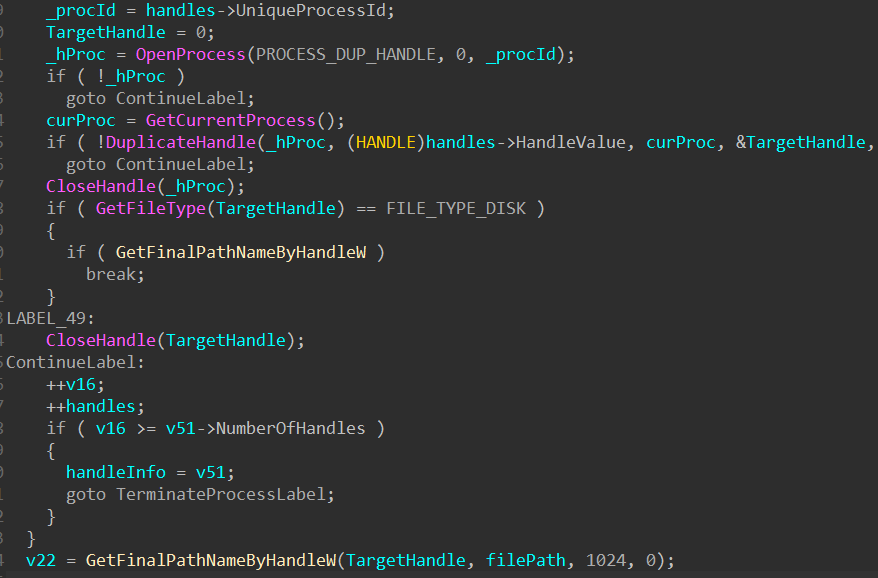
The actors have also removed the UAC requirement to maintain ‘Medium’ integrity, so they are going for less privileged folders, which are less likely to raise alarms. Files with open handles that can affect critical running processes (and, as such, risk detection) are also excluded thanks to a new system that performs some relevant queries first.
Other additions include a new system to avoid re-encrypting files that have been already encrypted by a previous Phobos version, the removal of quite a few redundant functions that raise the risk of detection for no good reason, and the implementation of a new system to support volumes spanning across multiple physical drives which adheres to the “best practices” as those defined by Microsoft. Finally, the use of ‘netsh’ to disable the firewall was removed, and all interactions with the OS were brought down to the minimum essential number and level.
Although Phobos as an encrypter is still considered unsophisticated, everything around it has gone up a level in stealthiness. This tells us that the particular actors are more focused on maintaining their foothold in valuable servers than on encrypting stuff and creating operational disruption. This aspect looks like a secondary function kept as an option for when espionage is over or discovered.