This Is How Phishing Actors Move to Grab Hosting Provider Accounts
2 min read- Phishing actors love to steal domains and do what they want with other people’s websites.
- The actual phishing sites and the emails are quite obviously fake, but they still trick those who lose their calm.
- Owners of hosting provider accounts are advised to act with sangfroid when met with bold suspension-related claims.
The reason why phishing actors like to target user accounts on hosting provider websites is simple, really, and it’s to tap on the subsequent, actual targets – the precious domains that are under the control of the compromised account. From there, the hackers may link to other content, update the site through a web interface, change the FTP password and fiddle with the content management, and more.
According to Kaspersky, cybercriminals today typically do this to set up convincing phishing pages, using valid domains, real content, and only performing some minor additions like forms and data exfiltration scripts.
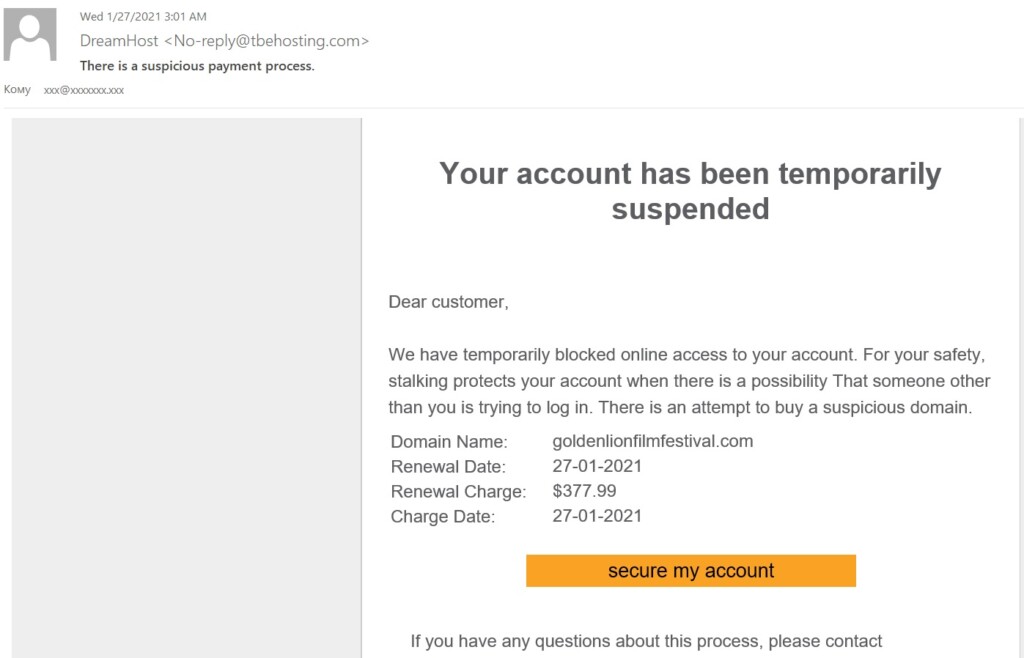
The process begins with the phishing email sent by the actors, which poses as a message from a hosting provider. There are no names or logos in there, so the crooks rely on the recipient’s panic.
The text informs them of a temporary blockage against accessing their accounts, supposedly because someone unsuccessfully attempted to log into it too many times. The rest of the generic info presented on the message body is taken from “WhoIs” services, and the goal is to trick the victim into following the link to the phishing site.
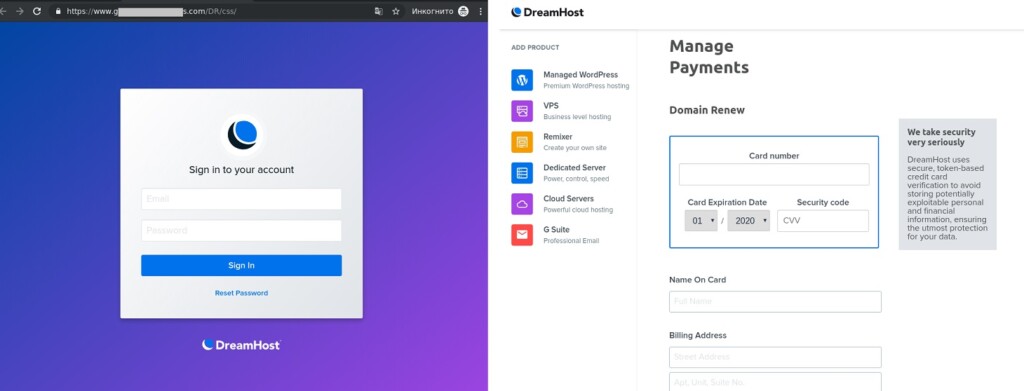
There, they will find a pretty unconvincing login page that looks as fake as it is. If the victimized account holder is still in panic mode, they will enter their credentials, card number and CVV, full name, billing address, and everything the actor needs to steal the domain.
All of this data is requested on the excuse that the account holder needs to verify themselves, their payment method, and their personal details, supposedly to confirm that it’s really that person, and give them the keys to the site back.
Whenever you receive emails that make claims of this kind, open a new tab, find the platform’s official website through Google search and log in on that page. If any messages need your attention, you will see them on the alerts.
Never follow buttons or links arriving via email, and never act hastily. Finally, if you haven’t already activated 2FA to protect your account, go ahead and do it right away.