- There’s a new ransomware strain out there, locking people’s computers to force them to join its Discord server.
- Users can grab a token from there and use it on the provided decrypter to get their files back.
- This is a worrying development for what it may become in the future, even if it’s currently tame.
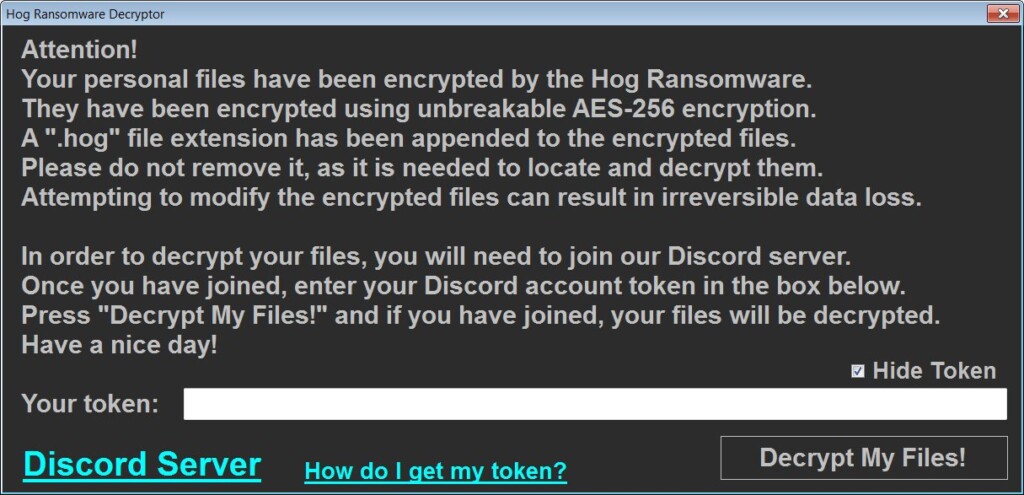
There’s a new ransomware strain circulating out there called “Hog” that encrypts users’ devices as a way to force them to join the developer’s Discord server. If they do, they get a decryption key so they can get their files back. The encryption is real and pretty strong (AES-256), so while the message appears somewhat humoristic to those reading it the first time, the actual situation is far from being lighthearted.
Once the encryption is completed and all of the victim’s files have the “.hog” extension appended to them, the ransomware will launch the “DECRYPT-MY-FILES.exe” program, which explains the situation. For the victim to decrypt the files, they will need to enter the Discord account token in the decrypter’s box, which they will get from joining the server.
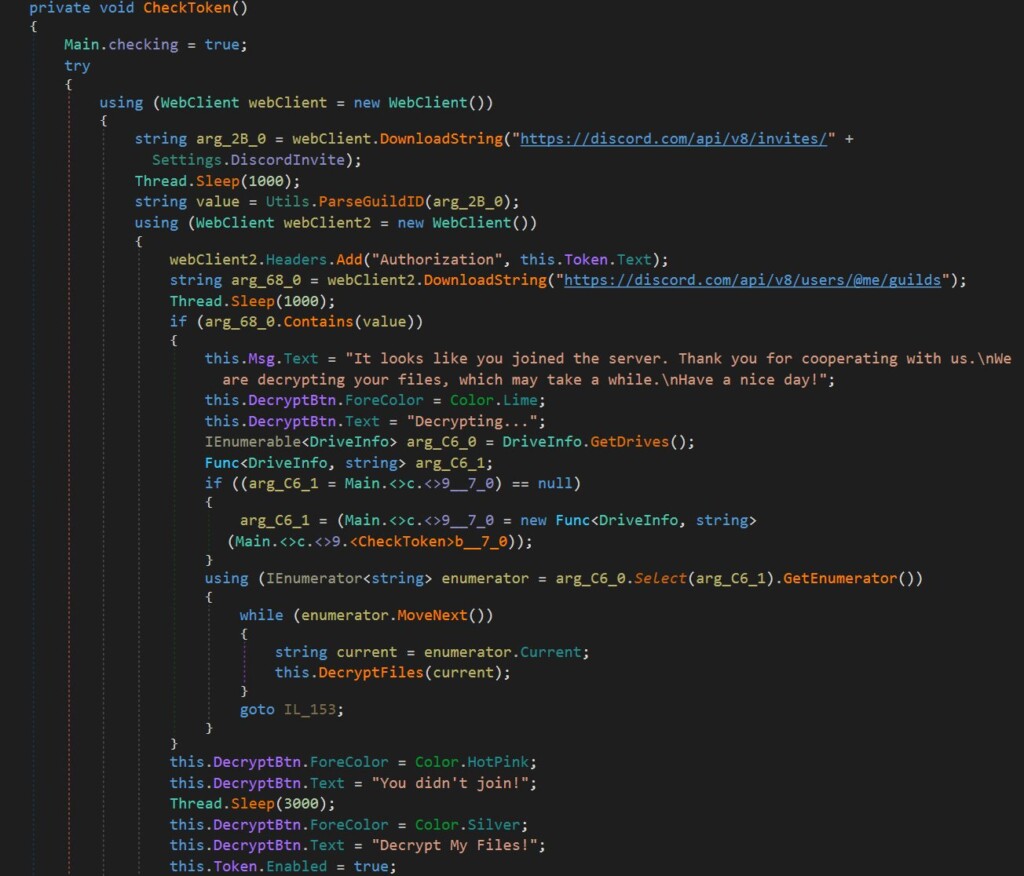
The program will then authenticate to the Discord’s API and check if they really joined the server. If they have, or if the server does not exist, the static key that’s embedded in the ransomware is activated, and the files are decrypted. These two details, the existence of a local key, and the defaulting to the user’s side if the server is offline make it almost certain that a free decrypter will be made available soon.
Just yesterday, we discussed how AlumniLocker, a pretty new ransomware strain, is abusing Discord for communications. In the case of Hog, we’re seeing a link to Discord again, although a qualitatively different one. The common ground is the fact that Discord seems to be unregulated and nasty things go generally unreported or at least not moderated.
While Hog may appear innocuous in practice, since its victims can easily get their files back, its existence rings many alarms. It could be at an early experimentation phase, and it could be just the first example of a new wave of ransomware strains that are asking for all kinds of weird things.
And finally, the process of encrypting with AES-256 and then decrypting the files back to their original form doesn’t guarantee that everything will return to pristine condition. On the contrary, errors in the process may render the files permanently irretrievable. For this reason, if you ever face an encryption of this or any level, make sure to take a backup of the encrypted files before you engage with the decrypter. Even if the process is as simple as entering a token, do not jump to it like that.
- CryptoQuant Analyst: Bitcoin Nowhere Near Its Peak – Buckle Up, Hodlers! - December 21, 2024
- Chainalysis: $2.2 Billion Lost to Crypto Hacks in 2024 - December 21, 2024
- Bank of Japan leaves interest rate unchanged: Impact on the macroeconomy and the crypto market - December 20, 2024