- Researchers discovered two critical flaws on SolarWinds Orion and one bug on Serv-U FTP.
- This throws more fuel in the fire that is burning the American software vendor.
- The vulnerabilities have been fixed, but the actual PoC will be released a little bit later to allow time for patching.
There’s a growing concern about the risks of closed-source software being deployed in critical environments following the supply chain attacks carried out through the SolarWinds Orion product. While the investigation on the impact and scope of these attacks is ongoing, researchers at Trustwave have found two critical flaws in the SolarWinds Orion platform and another one on SolarWinds Serv-U FTP. Those who have been calling for a shift to open source solutions have just gotten some strong backing for their arguments.
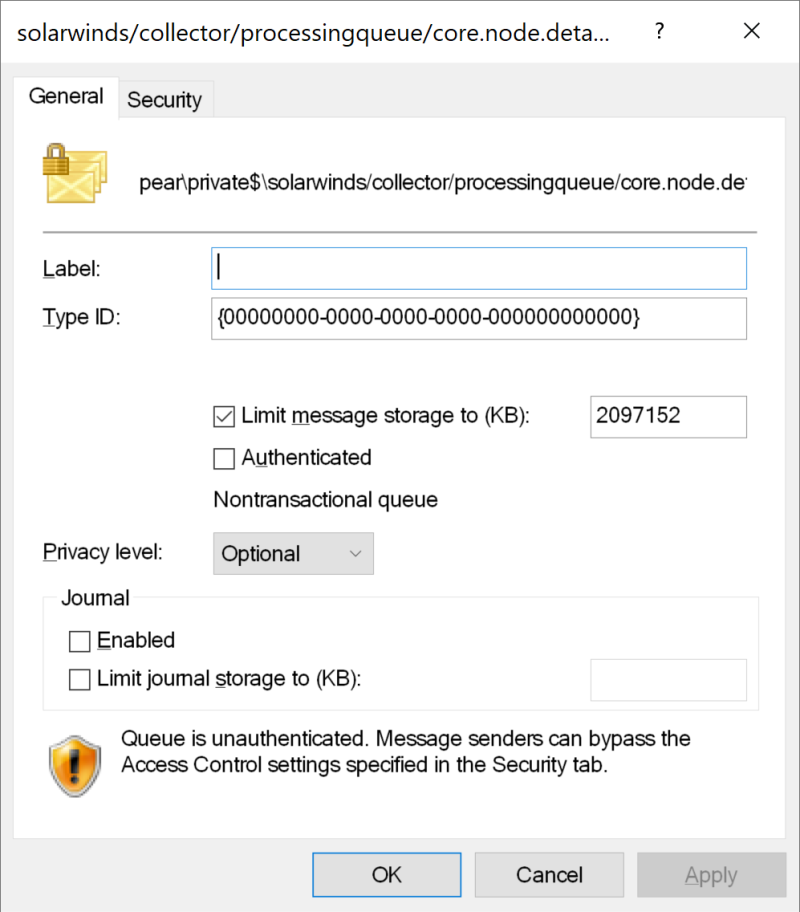
The first Orion flaw is CVE-2021-25274, and it is a remote code execution that is based on a combination of two issues. The proof of concepts describes the worrying ability to send messages to unauthenticated queues over TCP port 1801, without the user having to authenticate either.
The attacker can gain complete control of the underlying operating system as the message processing code runs as a Windows service that is configured to use the LocalSystem account.
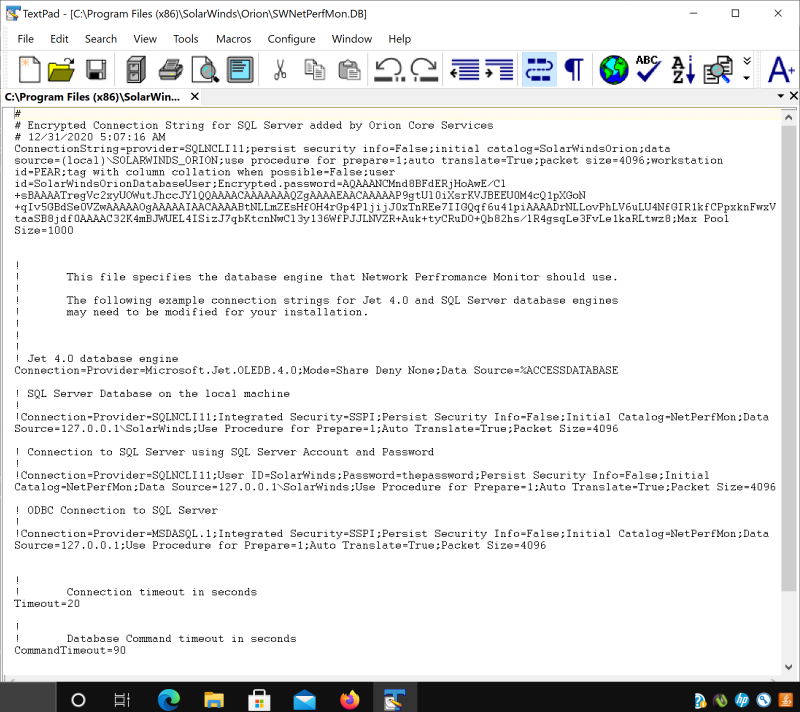
The second vulnerability is CVE-2021-25275, and it concerns a database credentials access problem. The researchers found that it’s fairly easy to access the database file on the products installation folder, as the permissions allow all users to open and read it.
While the contents are encrypted, deriving the cleartext password for the SolarWindsOrionDatabaseUser is also easy using a simple utility. From there, a low-level user can connect to the Microsoft SQL Server and take full control of the database.
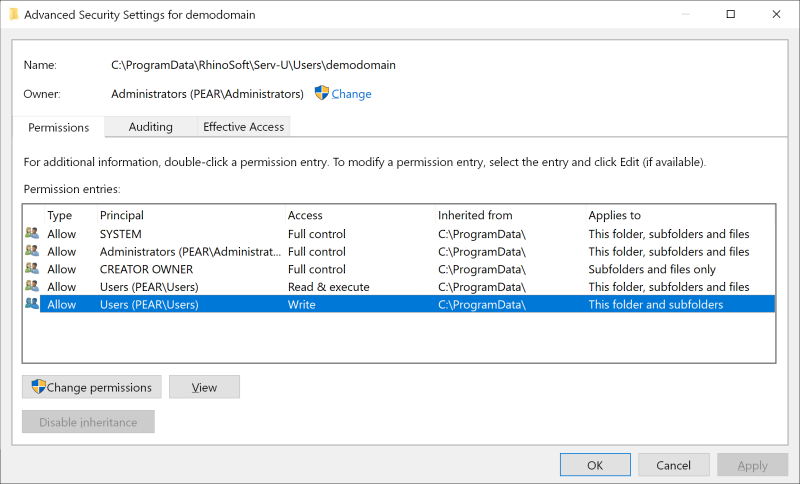
Finally, there’s CVE-2021-25276, which concerns the Serv-U FTP product for Windows. This bug practically allows users to create admin accounts under their ownership, log in via FTP, and then fiddle with whatever their want on the system disk as LocalSystem. The exploit also works via Remote Desktop, so the consequences are dire.
The Trustwave team found the two Orion flaws and disclosed them to SolarWinds on December 30, 2020, along with the PoC details. The Serv-U FTP bug was reported to the vendor on January 04, 2021.
SolarWinds eventually released the corresponding hotfixes on January 22 (Serv-U FTP) and January 25 (Orion), so the issues have been addressed. To keep your systems safe from the three flaws, upgrade to Orion 2020.2.4 and Serv-U FTP 15.2.2 Hotfix 1.
- CryptoQuant Analyst: Bitcoin Nowhere Near Its Peak – Buckle Up, Hodlers! - December 21, 2024
- Chainalysis: $2.2 Billion Lost to Crypto Hacks in 2024 - December 21, 2024
- Bank of Japan leaves interest rate unchanged: Impact on the macroeconomy and the crypto market - December 20, 2024