Table of Contents

Computers communicate using networks. These networks could be on a local area network LAN or exposed to the internet. Network Sniffers are programs that capture low-level package data that is transmitted over a network. An attacker can analyze this information to discover valuable information such as user ids and passwords.
In this article, we will introduce you to common network sniffing techniques and tools used to sniff networks. We will also look at countermeasures that you can put in place to protect sensitive information been transmitted over a network.
What is network sniffing?
Computers communicate by broadcasting messages on a network using IP addresses. Once a message has been sent on a network, the recipient computer with the matching IP address responds with its MAC address.
Network sniffing is the process of intercepting data packets sent over a network.This can be done by the specialized software program or hardware equipment. Sniffing can be used to;
- Capture sensitive data such as login credentials
- Eavesdrop on chat messages
- Capture files have been transmitted over a network
The following are protocols that are vulnerable to sniffing
- Telnet
- Rlogin
- HTTP
- SMTP
- NNTP
- POP
- FTP
- IMAP
Passive and Active Sniffing
Before we look at passive and active sniffing, let’s look at two major devices used to network computers; hubs and switches.
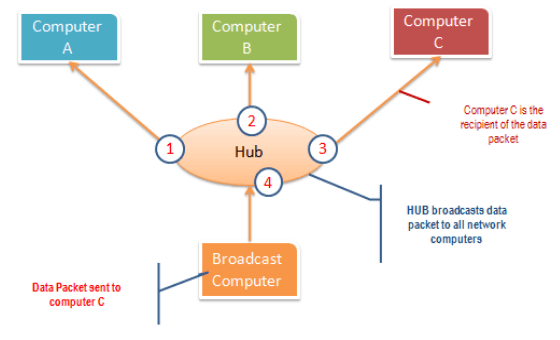
A hub works by sending broadcast messages to all output ports on it except the one that has sent the broadcast. The recipient computer responds to the broadcast message if the IP address matches. This means when using a hub, all the computers on a network can see the broadcast message. It operates at the physical layer (layer 1) of the OSI Model.
How the hub works.
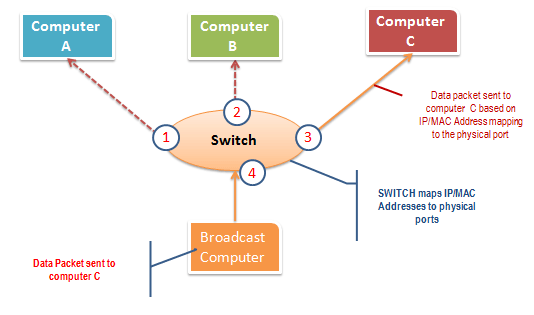
A switch works differently; it maps IP/MAC addresses to physical ports on it. Broadcast messages are sent to the physical ports that match the IP/MAC address configurations for the recipient computer. This means broadcast messages are only seen by the recipient computer. Switches operate at the data link layer (layer 2) and network layer (layer 3).
How the switch works.
Passive sniffing is intercepting packages transmitted over a network that uses a hub. It is called passive sniffing because it is difficult to detect. It is also easy to perform as the hub sends broadcast messages to all the computers on the network.
Active sniffing is intercepting packages transmitted over a network that uses a switch. There are two main methods used to sniff switch linked networks, ARP Poisoning, and MAC flooding.
What is Packets?
It turns out that everything you do on the Internet involves packets. For example, every Web page that you receive comes as a series of packets, and every e-mail you send leaves as a series of packets. Networks that ship data around in small packets are called packet switched networks.
On the Internet, the network breaks an e-mail message into parts of a certain size in bytes. These are the packets. Each packet carries the information that will help it get to its destination — the sender’s IP address, the intended receiver’s IP address, something that tells the network how many packets this e-mail message has been broken into and the number of this particular packet. The packets carry the data in the protocols that the Internet uses: Transmission Control Protocol/Internet Protocol (TCP/IP). Each packet contains part of the body of your message. A typical packet contains perhaps 1,000 or 1,500 bytes.
How to Use Wireshark to Capture, Filter and Inspect Packets
Wireshark, a network analysis tool formerly known as Ethereal, captures packets in real time and display them in human-readable format. Wireshark includes filters, color coding, and other features that let you dig deep into network traffic and inspect individual packets.
- You can download Wireshark for Windows or macOS from its official website. If you’re using Linux or another UNIX-like system, you’ll probably find Wireshark in its package repositories. For example, if you’re using Ubuntu, you’ll find Wireshark in the Ubuntu Software Center.
Capturing Packets
After downloading and installing Wireshark, you can launch it and double-click the name of a network interface under Capture to start capturing packets on that interface. For example, if you want to capture traffic on your wireless network, click your wireless interface. You can configure advanced features by clicking Capture > Options, but this isn’t necessary for now.
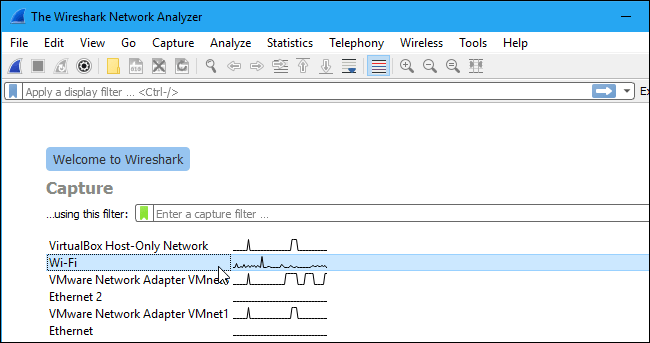
As soon as you click the interface’s name, you’ll see the packets start to appear in real time. Wireshark captures each packet sent to or from your system.
If you have promiscuous mode enabled—it’s enabled by default—you’ll also see all the other packets on the network instead of only packets addressed to your network adapter. To check if promiscuous mode is enabled, click Capture > Options and verify the “Enable promiscuous mode on all interfaces” checkbox is activated at the bottom of this window.
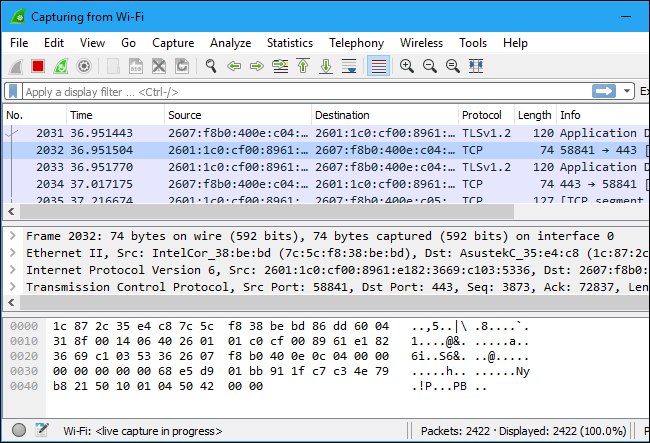
Open your web browser and type your desired site using http protocol.
Click the red “Stop” button near the top left corner of the window when you want to stop capturing traffic.
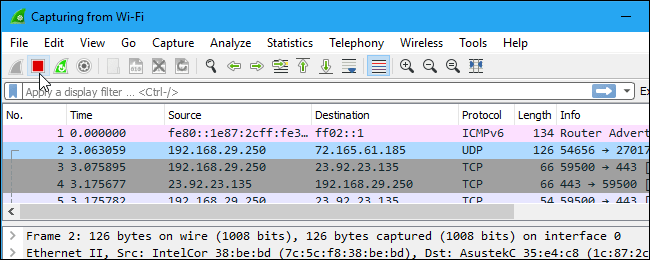
Color Coding
You’ll probably see packets highlighted in a variety of different colors. Wireshark uses colors to help you identify the types of traffic at a glance. By default, light purple is TCP traffic, light blue is UDP traffic, and black identifies packets with errors—for example, they could have been delivered out of order.
To view exactly what the color codes mean, click View > Coloring Rules. You can also customize and modify the coloring rules from here, if you like.
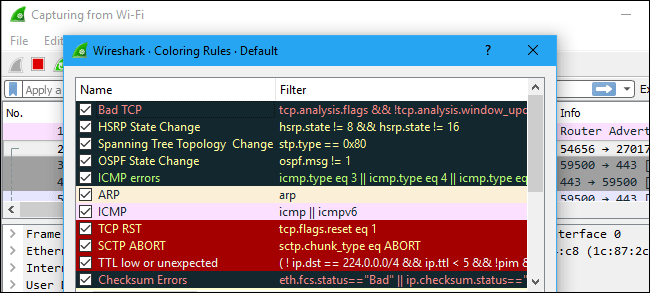
Filtering Packets
If you’re trying to inspect something specific, such as the traffic a program sends when phoning home, it helps to close down all other applications using the network so you can narrow down the traffic. Still, you’ll likely have a large amount of packets to sift through. That’s where Wireshark’s filters come in.
The most basic way to apply a filter is by typing it into the filter box at the top of the window and clicking Apply (or pressing Enter). For example, type “http” and you’ll see only HTTP packets. When you start typing, Wireshark will help you autocomplete your filter.
- Locate the Info column and look for entries with the HTTP verb POST and click on it .
You can also click Analyze > Display Filters to choose a filter from among the default filters included in Wireshark. From here, you can add your own custom filters and save them to easily access them in the future.
You can build display filters that compare values using a number of different comparison operators. For example, to only display packets to or from the IP address 192.168.0.1, use ip.addr==192.168.0.1.
Just below the log entries, there is a panel with a summary of captured data.
You should be able to view the plaintext values of all the POST variables submitted to the server via HTTP protocol.
What is a MAC Flooding?
MAC flooding is a network sniffing technique that floods the switch MAC table with fake MAC addresses. This leads to overloading the switch memory and makes it act as a hub. Once the switch has been compromised, it sends the broadcast messages to all computers on a network. This makes it possible to sniff data packets as they sent on the network.
Counter Measures against MAC flooding
- Some switches have the port security feature. This feature can be used to limit the number of MAC addresses on the ports. It can also be used to maintain a secure MAC address table in addition to the one provided by the switch.
- Authentication, Authorization and Accounting servers can be used to filter discovered MAC addresses.
Sniffing Counter Measures
- Restriction to network physical media highly reduces the chances of a network sniffer been installed
- Encrypting messages as they are transmitted over the network greatly reduces their value as they are difficult to decrypt.
- Changing the network to a Secure Shell (SSH)network also reduces the chances of the network been sniffed.
Summary
- Network sniffing is intercepting packages as they are transmitted over the network
- Passive sniffing is done on a network that uses a hub. It is difficult to detect.
- Active sniffing is done on a network that uses a switch. It is easy to detect.
- MAC flooding works by flooding the MAC table address list with fake MAC addresses. This makes the switch to operate like a HUB
- Security measures as outlined above can help protect the network against sniffing.
- A Look Back at Bitcoin’s Historic Year 2024: From ETFs to New All-Time Highs - December 31, 2024
- Ethereum Price Could Skyrocket in 2025: Here’s What Experts Expect 🚀📊 - December 31, 2024
- How Trump’s Politics Could Send Ethereum to the Moon—Or Just to Mar-a-Lago? - December 30, 2024