Table of Contents
There was a recent ransomware attack on Florida software vendor Kaseya, with hackers demanding a ransom of $ 50 million (less than the previously required $ 70 million) in exchange for restoring data access.
Kaseya provides software services to thousands of clients around the world. The attack is estimated to affect 800 to 1,500 SMEs The global ransomware attack has been identified as the largest recorded and the alleged culprit is the Russian cybercrime organization REvil.
Despite their fame, no one really knows what REvil is, what they are capable of or why they do what they do – except for the immediate benefit of huge sums of money. Ramsorware attacks also often involve large-scale distributed networks, so it’s not even certain that the individuals involved knew each other.
Attacks are growing exponentially in size and demand for ransom and are gradually changing the way we operate online. Many do not perceive them as a threat, because it cannot happen to them, they even admire their work. Understanding who these groups are and what they want is crucial to blowing them up.
Here is a list of the five most dangerous online criminal organizations. As far as we know, these groups are not supported or sponsored by any state.
Keeps the world in check for ransom: Top 5 online gangs
DarkSide
DarkSide is the group behind the attack on the Colonial Pipeline in May, which stopped the US fuel distribution network, raising concerns about fuel shortages.
The group first appeared in August last year. It targets large companies, causing them to disrupt their services – a key factor because they are more likely to pay ransom. These companies are also more likely to have cyber insurance, which makes it easy for criminals to make money.
The DarkSide model is to offer a service. In other words, they carry out ransomware attacks on behalf of other perpetrators so that they can reduce their liability. Then they share the profits. The group, which offers cybercrime as a service, also provides online communication in forums to support others who may want to improve their cybercrime skills.
This may involve teaching someone how to combine distributed denial of service (DDoS) and ransomware attacks to put further pressure on action. Ransomware would prevent the company from working on past and current orders, while a DDoS attack would block any new orders.
REvil
The REvil group is currently on the front pages due to the ongoing Kaseya incident and another recent attack on JBS meat processors. This group was particularly active in 2020-2021.
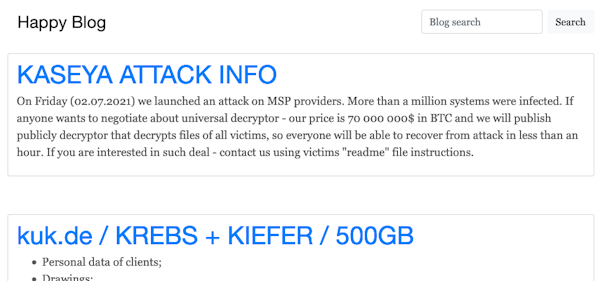
In April, REvil stole technical data on unreleased Apple products from Taiwanese company Quanta Computer, which makes Apple laptops. In order to prevent the public disclosure of the stolen data, a ransom of 50 mil. USD. It was not revealed whether this money was paid out or not.
Clop
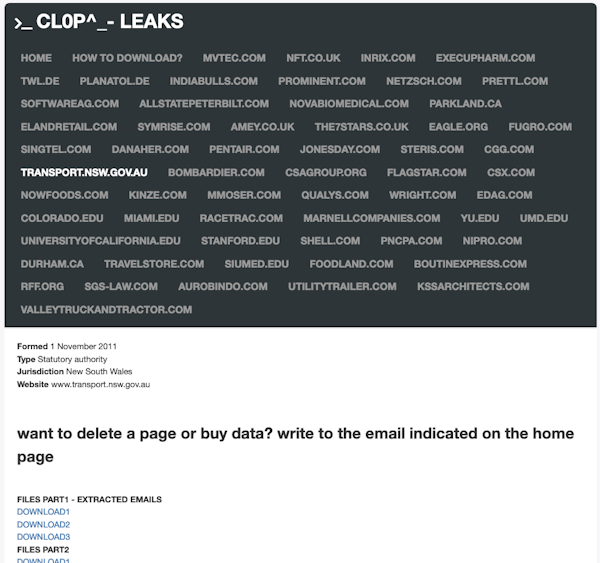
The ransomware group Clop, created in 2019, is responsible for revenue of half a billion US dollars.
The specialty of the Clop group is “double blackmail”. This includes targeting organizations with a ransom for a decryption key that restores the organization’s access to the stolen data. However, the targets must then pay another ransom so that the data is not published.
Historical examples show that organizations that pay ransom once are most likely to pay again in the future. So hackers will tend to target the same organizations over and over again, demanding more money each time.
Syrian Electronic Army
The Syrian e-army has been conducting online attacks in support of political propaganda since 2011. They have been called a hactivist group with this motive. The group has ties to the regime of Bashar al-Assad and is trying to be a media assistant to the Syrian army.
Their technique is to distribute fake messages through reputable sources. In 2013, their only tweet sent from the official account of the Associated Press, the world’s leading news agency, caused billions to be erased from the stock market.
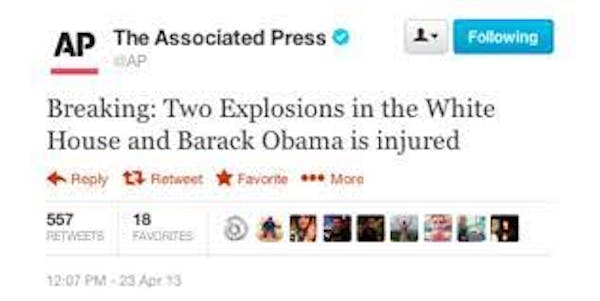
The Syrian e-military takes advantage of the fact that most people tend to interpret and respond to content with an implicit sense of trust.
FIN7
If this list could contain a “super villain”, it would be FIN7. Another Russian group is probably the most successful online criminal organization of all time. It has been operating since 2012.
Many of their operations have not been identified for many years. They use cross-attack scenarios where data breaches serve a variety of purposes. For example, it may allow for ransom by ransom while allowing an attacker to use data against victims, for example by reselling it to a third party.
In early 2017, FIN7 was reportedly behind the attack on companies filing submissions with the US Securities and Exchange Commission. This confidential information was used and used to obtain a ransom, which was then invested on the stock exchange.
As such, the group made huge sums of money by trading confidential information. The trading scheme facilitated by hacking has continued for many years – so it is not possible to quantify the exact amount of economic damage. However, it is estimated to exceed $ 1 billion.
Organized criminals
When it comes to complex criminal organizations, techniques are evolving and motives vary.
The way they organize and commit crimes online is very different from the offline gang. Ransomware can be run from anywhere in the world, making it very difficult to prosecute these criminals. Matters are even more complicated when several parties coordinate across borders.
No wonder the problem for law enforcement is significant. It is essential that the authorities investigating the attack are certain that it was actually committed by someone they suspect. But to know that, they need all the help they can get.
- What Could Bitcoin’s Price Be in 25 Years? A Lambo or Just a Latte?” 🚀💸 - December 23, 2024
- Solana Price Analysis – December 18, 2024: The Slippery Slope of SOL 🚀📉 - December 18, 2024
- Bitcoin Price Analysis – 16/12/2024: A Dance in the Ascending Channel - December 16, 2024
























