Understand why the biggest thefts of cryptocurrencies are in bridges
4 min read
More than $1.6 billion worth of cryptocurrencies have already been stolen from decentralized finance, or DeFi, bridges in 2022.
For those who don’t know – and don’t even have the obligation to know, bridges are protocols used to migrate assets from one blockchain to another. For example, they are responsible for enabling the migration of ETH on the ETH network to wETH on another blockchain.
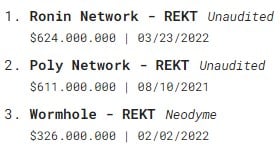
The biggest theft of the cryptocurrency market occurred through the breach of a bridge in March: the sad episode of Ronin. About $624 million was stolen by a group of North Korean hackers known as the Lazarus Group.
The third biggest hack in this market also occurred due to a security breach in a bridge. This is the Wormhole episode with a connection to Solana, from which about US$ 326 million was extracted. Although the bridge was bailed out by Jump Capital and the amount refunded, the episode hurt.
What remains in the air is the question: why is it so easy to neck in bridges? Well, for that you need to understand the current state of DeFi transactions and the most popular model for token migration. Let’s start with the second.
The synthetic asset model
The most popular way to migrate assets across bridges is to create synthetic assets. A synthetic asset is a representation of a native cryptocurrency, such as BTC and ETH, on another blockchain.
The model most used by bridges to create synthetic assets is known as Lock + Mint and Burn. Simply put, the process works as follows:
- You need to migrate ETH from ETH to the Solana network. The bridge has an ETH compatible part (EVM Compatible), where there is a smart contract;
- This smart contract receives the ETH and locks the funds. A message is sent to the other end of the bridge, asking for the issuance (mint) of the same amount of synthetic ETH inside the Ronin. This is how wETH came about;
- Part of that wETH is spent on Solana and you have a little money left over, which you want to go back to being ETH. At the bridge, the transfer back to the ETH network is made, and the wETH is burned.
The saying goes: “I don’t want to know who painted the zebra, but I want to know what paint is left”. In the above process, an ETH balance was stopped in the smart contract inside the bridge.
Imagine thousands of users doing this process. Well, a hefty sum is stuck in the smart contract. I know it, you know it. Hackers know too.
For this reason, bridges attract a lot of attention from bad actors. they are the famous honeypotshoney pots full of cash waiting to be drained.
Okay, it’s clear why bridges attract attention. Now, on to the security part. We will do this by looking at the current state of DeFi transactions.
Covers the saint’s head, the feet are uncovered
The number of DeFi users today is much higher than that recorded in “Summer 2020”. This name is given to the period in which decentralized finance exploded in popularity.
As we know and I’m not going to rain on the wet, ETH fees are expensive. Not everyone wants to pay $50 in fees to add liquidity to a pool. Developer teams around the world know this too, and then the race for scalability begins.
Simply put, scalability is the ability of a system to function even when the information load increases in volume. In other words, it’s a race to see which blockchain processes more transactions faster and cheaper.
Still speaking in a simplified way, it is much easier to pass information to five people than to 5 thousand. If I, a young country boy, know this, smart developers in the big city know it too.
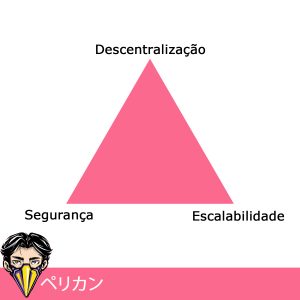
What happens is: to process information faster and cheaper, decentralization is sacrificed. Along with it, security is also delivered. We then violated what Vitalik Buterin, co-creator of ETH and owner of the world’s largest cubic area, called the “Blockchain Trilemma”.
According to this concept, blockchain needs: scalability, security and decentralization. It’s easy to reduce the number of nodes on the network and make information run faster. The increase in scalability, however, came at the expense of decentralization.
In the Blockchain Trilemma, this cannot happen. Never. The three points must be developed equally. I fix things better with images, so I made one for you:
What does one thing have to do with the other?
When $600 million is stored in one place, it seems ridiculous that the network has only nine validators. Even more ridiculous is the idea that a blockchain exposed to the public depends on the consensus of just five of these validators.
I hate being a turnkey engineer, but Sky Mavis, the company behind the network, had plenty of time to improve this. This neglect, however, occurs in many other applications. The example of the reduced number of validators is just one of them.
Also, important security details are ignored in order to quickly drop a solution to market. The race for profits, so far, has trumped the race for fundamentals.
It is certain that bridges will never stop being honeypots. However, as long as more security efforts are not directed, it will be neck after neck until we have other interoperability solutions.
So, summarizing all that has been said:
- There is a lot of money sitting in bridges, so they will continue to be the target of attacks;
- The high capacity of different blockchains has been achieved through the sacrifice of decentralization and security. This practice, as time has shown, is unhealthy.






