- Zimperium recorded a huge rise in mobile phishing attack rates in 2020.
- Threat actors are turning their attention to remote workers who don’t pay attention to security.
- The phishing domains used by the actors stayed online for almost a month.
Zimperium, the mobile security expert, has compiled a report about all that happened in the space during 2020, how the COVID-19 situation has affected mobile phishing rates, why mobile users are most vulnerable than ever before, and how the human factor comes into play when security alarms go off.
First of all, the frequency of phishing attacks has increased six-fold, as malicious actors have turned their attention to the mobile space. Zimperium has caught many instances of this kind (since its mobile security solutions are being deployed in millions of devices globally) and tells us that one-third of users who were warned they’re about to land on a phishing site still tapped on the link.
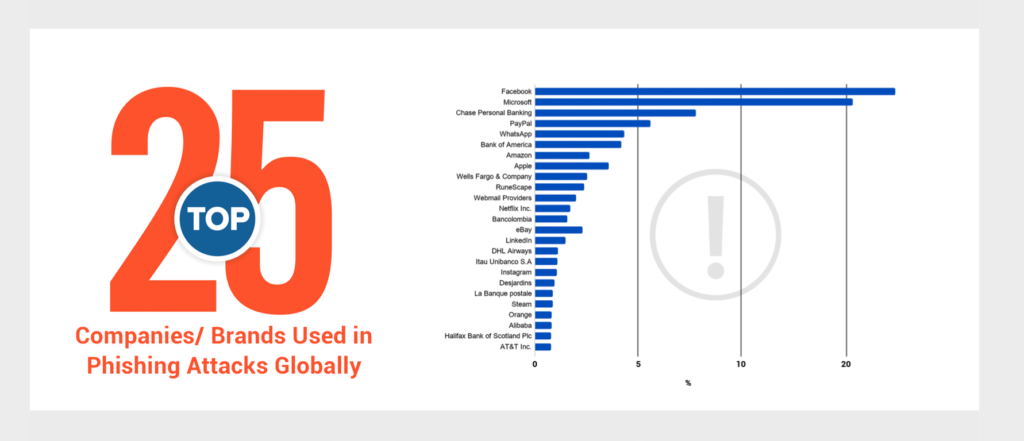
The most impersonated brands are Facebook, Microsoft, Chase, Paypal, WhatsApp, the Bank of America, and Amazon, but this varies based on the region. For example, in Russia, the most frequently spoofed entity is Steam. In Brazil, it’s ‘Americanas.com.’
In the United States, the most common phishing theme is Office365, targeting remote workers who are looking to log in to their Microsoft accounts.
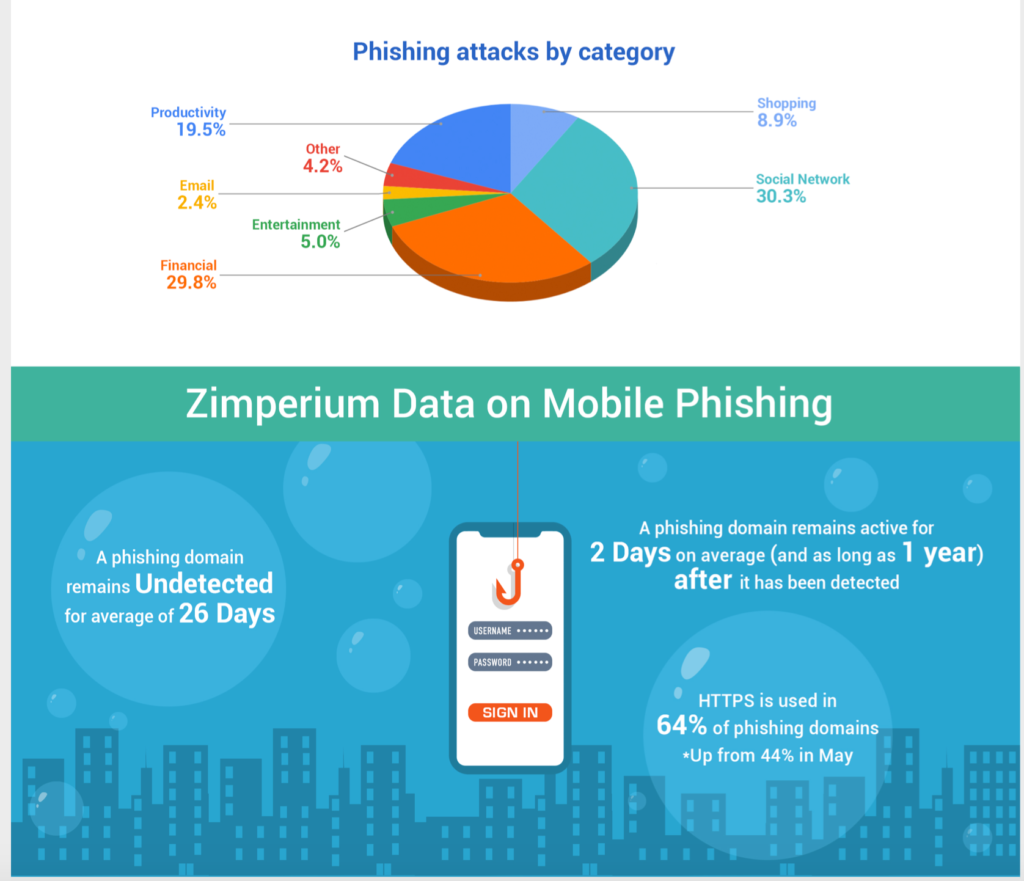
As the report details, a phishing domain in 2020 remained undetected (and unreported) for an average of 26 days, while the average identification and reporting time was 24 days. Some extreme cases went on for the entire year, though, so sometimes things can stray far from the typical.
Worryingly, HTTPS was used in 64% of the identified cases, creating a false sense of security and legitimacy to the victims.
This should make it clear to you that your mobile device is neither spared from threat actors nor intrinsically safe from risks that can quickly develop into “out of control” situations. The most effective method to stay safe from these threats is to install a complete mobile security solution from a reputable vendor – and then to pay attention to the generated warnings, of course.